Remember our rollercoaster ride through the world of APIs? Well, strap in again, because we’re about to embark on another thrilling journey. This time, we’re exploring the treacherous terrains of API2:2023 Broken Authentication. Hold onto your keyboards, it’s going to be a bumpy ride! 🎢
| “When your API’s authentication be like…" |
🏰 The Fortress Under Siege: Broken Authentication
Setting: The grand castle of APIs, where authentication acts as the mighty drawbridge, allowing only the worthy to enter.
The Flaw: Unfortunately, the drawbridge has some loose planks. Attackers, with their cunning and tools, can exploit these weaknesses, gaining unauthorized access to the castle’s treasures.
The Drama: While the castle guards (software engineers) believe the fortress is impregnable, attackers find crafty ways to breach the walls, causing chaos within.
🛠️ Behind the Castle Walls: The Code
Backend Code (Before Fix):
@app.route('/login', methods=['POST'])
def login():
username = request.json.get('username')
password = request.json.get('password')
user = User.authenticate(username, password)
if user:
token = generate_token(user)
return jsonify(token=token)
return "Invalid credentials!", 401
This code simply checks the provided credentials and, if valid, grants an access token. But there’s no mechanism to prevent brute force attacks or rate limit login attempts.
Backend Code (After Fix):
from flask_limiter import Limiter
limiter = Limiter(app, key_func=get_remote_address)
@app.route('/login', methods=['POST'])
@limiter.limit("5 per minute")
def login():
username = request.json.get('username')
password = request.json.get('password')
user = User.authenticate(username, password)
if user:
token = generate_token(user)
return jsonify(token=token)
return "Invalid credentials!", 401
With the fix, the backend now uses Flask’s rate limiting to restrict login attempts, making brute force attacks much harder.
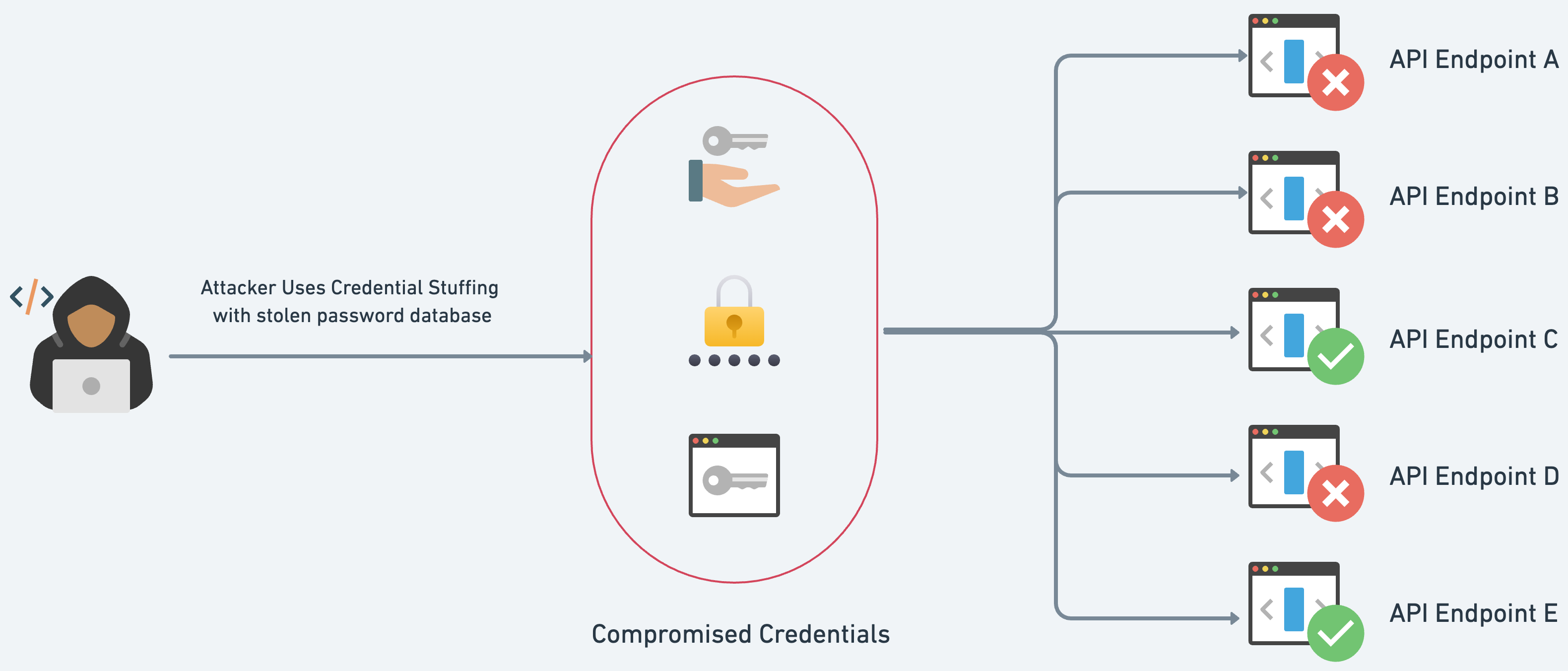
🎭 The Intruders' Tactics: Attack Scenarios
Scenario #1: On the “ChirpChirp” platform, attackers discover they can batch multiple login attempts in a single request, bypassing rate limits. By sending arrays of login attempts, they can guess passwords at lightning speed!
Scenario #2: On the same platform, attackers find that they can change a user’s email without re-authentication. With just an access token, they can hijack accounts, redirecting password resets to their own email addresses.
 |
|---|
| When you bypass authentication like a king |
🎥 Spotlight: The “PhotoSnap” Fiasco
Setting: “PhotoSnap”, a popular photo-sharing platform where users can upload, share, and comment on photos. Each user has a unique username and password to access their account.
The Flaw: PhotoSnap’s API endpoint for logging in is /api/login, which accepts a username and password. The backend checks these credentials and, if valid, returns an access token. However, there’s no mechanism to prevent multiple rapid login attempts, making it susceptible to brute-force attacks.
The Exploit: Charlie, a curious hacker, realizes that he can send hundreds of login requests per second to guess the passwords of users. Using a list of common passwords, he targets Alice’s account, attempting to log in with different passwords until he finds the right one.
🛠️ The Code Behind the Curtain
Backend Code (Before Fix):
@app.route('/api/login', methods=['POST'])
def login():
username = request.json.get('username')
password = request.json.get('password')
user = User.authenticate(username, password)
if user:
token = generate_token(user)
return jsonify(token=token)
return "Invalid credentials!", 401
This code simply checks the provided credentials and, if valid, returns an access token. But there’s no mechanism to prevent or slow down multiple login attempts.
Backend Code (After Fix):
from flask_limiter import Limiter
limiter = Limiter(app, key_func=get_remote_address)
@app.route('/api/login', methods=['POST'])
@limiter.limit("5 per minute")
def login():
username = request.json.get('username')
password = request.json.get('password')
user = User.authenticate(username, password)
if user:
token = generate_token(user)
return jsonify(token=token)
return "Invalid credentials!", 401
With the fix, the backend now uses Flask’s rate limiting to restrict login attempts to 5 per minute, making brute force attacks much more challenging.
🎭 The Drama Unfolds
Charlie tries his rapid-fire login attempts again. This time, after just five attempts, he’s locked out for a minute. His brute force script becomes ineffective, and Alice’s account remains secure. PhotoSnap users can now share their memories without the fear of unauthorized access.
 |
|---|
| “When rate limiting ruins your day” |
This “PhotoSnap” example showcases the importance of implementing rate limiting and other security measures in authentication endpoints. It’s a reminder that even popular platforms can have vulnerabilities, and continuous security assessments are crucial.
🏰 Fortify the Castle: Defense Strategies
- Know Your Entry Points: Understand all authentication flows. Whether it’s mobile, web, or one-click authentication, be aware!
- Trust, but Verify: Familiarize yourself with authentication mechanisms. OAuth and API keys aren’t the same as user authentication.
- Use Proven Tools: Don’t craft your own authentication or password storage. Stick to tried-and-true standards.
- Guard the Drawbridge: Treat “Forgot password” endpoints with the same security as login endpoints.
- Double-Check Identity: For sensitive operations, always re-authenticate.
- Embrace Multi-Factor: Where possible, add an extra layer of security with multi-factor authentication.
- Bolster Defenses: Implement anti-brute force mechanisms, weak-password checks, and account lockouts.
- Distinguish Keys: API keys are for client authentication, not user authentication.
📚 Chronicles of the Castle: Further Reading
- OWASP’s Grand Library:
- External Sagas:
In the ever-evolving realm of APIs, the battle between defenders and attackers rages on. But with knowledge, vigilance, and the right tools, the castle can stand strong. Until our next adventure, code safely and guard your gates! 🏰🔐
 |
|---|
| “To secure APIs and peaceful nights!" |