Remember our thrilling rides through the API amusement park? Well, buckle up, because we’re about to embark on another electrifying journey. This time, we’re diving deep into the murky waters of API3:2023 Broken Object Property Level Authorization. Grab your detective hats, because there’s a mystery to solve! 🕵️♂️
 |
|---|
| When your API’s properties spill secrets.. |
🕳️ The Plot Thickens: Broken Object Property Level Authorization
Setting: The bustling city of APIville, where every object has properties, and some of these properties are like hidden alleyways, meant to be kept secret.
The Flaw: Some APIs, in their eagerness to be helpful, overshare. They expose more properties than they should, giving away secrets that were meant to be kept under wraps.
The Drama: While the city’s architects (developers) believe they’ve built a secure environment, crafty thieves find hidden doors and windows, sneaking in to steal or manipulate valuable information.
 |
|---|
| Mass Assignment |
 |
|---|
| Excessive Data Exposure |
🛠️ The Blueprint: Code Exposed
Backend Code (Before Fix):
@app.route('/api/reportUser', methods=['POST'])
def report_user():
user_id = request.json.get('userId')
reason = request.json.get('reason')
reported_user = User.get_by_id(user_id)
if reported_user:
# ... (reporting logic) ...
return jsonify(status="Success", message="User reported", reportedUser=reported_user.to_dict())
return "User not found!", 404
This code, when reporting a user, also returns the reported user’s full details, including sensitive properties like fullName and recentLocation.
Backend Code (After Fix):
@app.route('/api/reportUser', methods=['POST'])
def report_user():
user_id = request.json.get('userId')
reason = request.json.get('reason')
reported_user = User.get_by_id(user_id)
if reported_user:
# ... (reporting logic) ...
safe_response = {
"id": reported_user.id,
"username": reported_user.username
}
return jsonify(status="Success", message="User reported", reportedUser=safe_response)
return "User not found!", 404
With the fix, the backend now only returns a safe subset of the reported user’s properties, ensuring that sensitive information remains hidden.
🎭 The Intrigue: Real-World Shenanigans
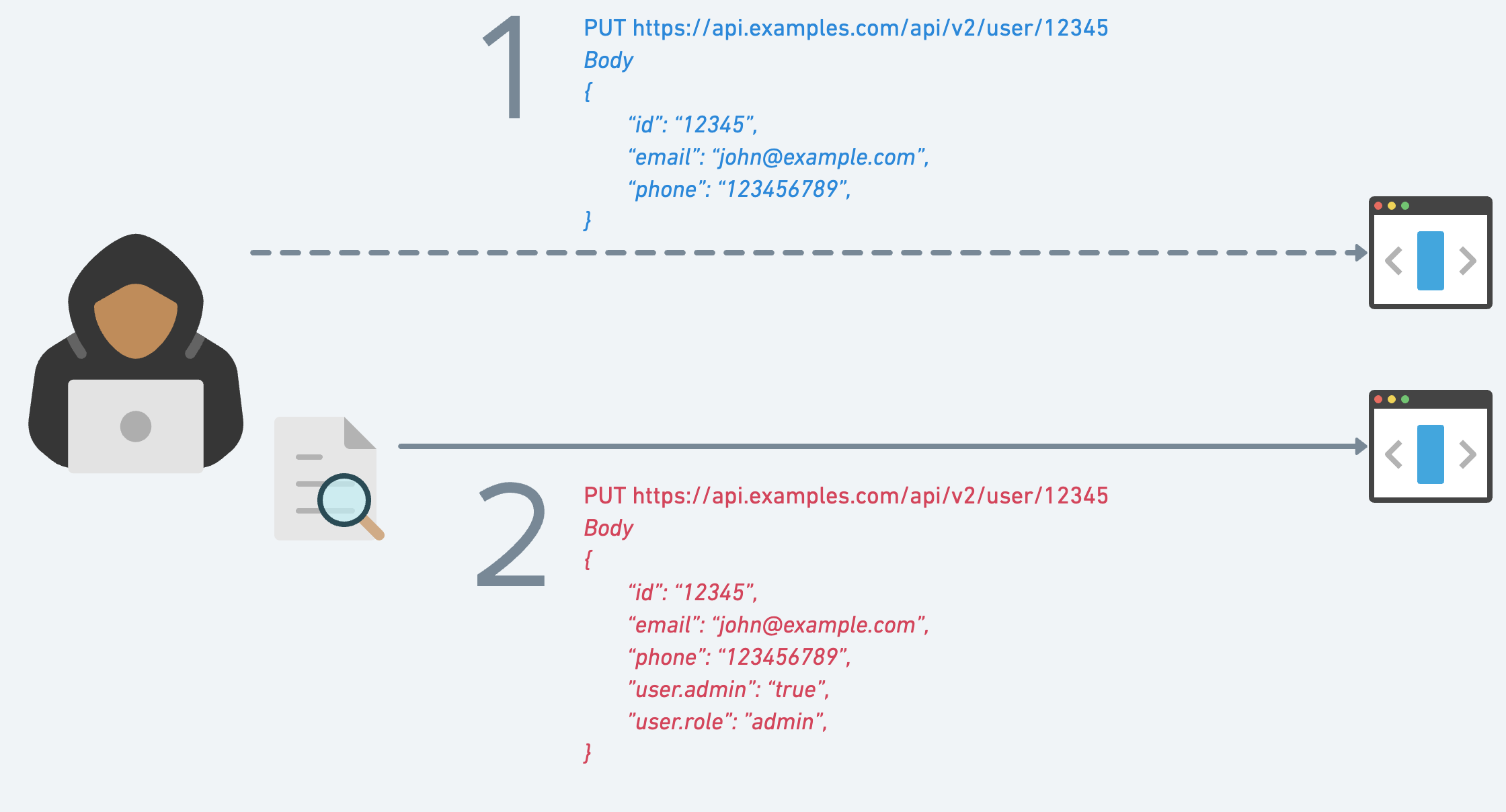
Scenario #1: On “DateMate”, a dating app, users can report inappropriate behavior. But when doing so, they unintentionally get access to the reported user’s full name and recent location. It’s like reporting a pickpocket and getting their home address in return!
Scenario #2: On “StayNPay”, an online rental platform, hosts can approve guest bookings. But a crafty host discovers they can also set their own price, turning their humble abode into a million-dollar mansion overnight!
Scenario #3: “VidShare”, a video platform, blocks inappropriate content. But a sneaky user finds a way to unblock their own videos, turning the platform into their personal, unfiltered stage.
 |
|---|
| “Hacking into properties like…" |
🎥 Spotlight: The “BookNook” Blunder
Setting: “BookNook”, a digital library where users can borrow and review books. Each book has properties like title, author, and borrower reviews. Some books also have a hidden property: restricted, which marks them as accessible only to premium members.
The Flaw: When users review a book on BookNook, they send their review text to the server. However, the server doesn’t strictly validate the incoming data, allowing users to send additional properties in their request.
The Exploit: Eve, a regular user, discovers that she can not only send her review but also modify the restricted property of a book. By doing so, she gains access to premium books without a subscription.
🛠️ The Code Behind the Curtain
Backend Code (Before Fix):
@app.route('/api/reviewBook', methods=['POST'])
def review_book():
book_id = request.json.get('bookId')
review_text = request.json.get('reviewText')
book = Book.get_by_id(book_id)
if book:
book.add_review(review_text)
# Vulnerable code: blindly updating all properties sent in the request
for key, value in request.json.items():
setattr(book, key, value)
book.save()
return "Review added and book updated!"
return "Book not found!", 404
This code not only adds the user’s review but also updates any property of the book that’s sent in the request, leading to the mass assignment vulnerability.
Backend Code (After Fix):
@app.route('/api/reviewBook', methods=['POST'])
def review_book():
book_id = request.json.get('bookId')
review_text = request.json.get('reviewText')
book = Book.get_by_id(book_id)
if book:
book.add_review(review_text)
# Secure code: only updating the properties we expect
if 'newTitle' in request.json:
book.title = request.json.get('newTitle')
book.save()
return "Review added and book updated!"
return "Book not found!", 404
With the fix, the backend now only updates specific properties that it expects, preventing users from modifying properties they shouldn’t have access to.
🎭 The Drama Unfolds
Eve tries her trick again, attempting to access a premium book by modifying its restricted property. This time, the server ignores her sneaky property modification. The premium book remains locked away, and BookNook’s library remains secure for all its users.
 |
|---|
| “No sneaky tricks in my library!" |
This “BookNook” example highlights the dangers of mass assignment in APIs. It’s crucial to always validate incoming data and only update the properties you expect.
🔍 Clues to Fortify: Defense Strategies
- Guard the Secrets: Always validate which object properties a user can access.
- Be Selective: Avoid generic methods that spill all the beans. Choose which properties to expose.
- Lock the Doors: Don’t let users modify properties they shouldn’t touch.
- Schema Safeguard: Implement a schema-based response validation to ensure only the right data gets out.
- Minimalism is Key: Keep data structures lean and mean. Only return what’s absolutely necessary.
📚 The Detective’s Handbook: Further Reading
- OWASP’s Detective Academy:
- External Chronicles:
In the sprawling cityscape of APIs, secrets lurk in every corner. But with a keen eye and the right tools, you can keep those secrets safe. Until our next detective adventure, code securely and keep those alleyways locked! 🔍🔐
 |
|---|
| On the lookout for secure APIs! |