Remember our previous escapades through the intricate world of APIs? Well, brace yourselves, because today we’re diving into the treacherous waters of API4:2023 Unrestricted Resource Consumption. Ready to embark on this thrilling journey? Let’s unravel the mystery! 🕵️♂️
 |
|---|
| “Nom nom nom… more resources!" |
🍔 The All-You-Can-Eat Buffet: Unrestricted Resource Consumption
Setting: The bustling digital city of APItopia, where every API serves a delicious buffet of data. But some buffets don’t have limits, and that’s where things get messy.
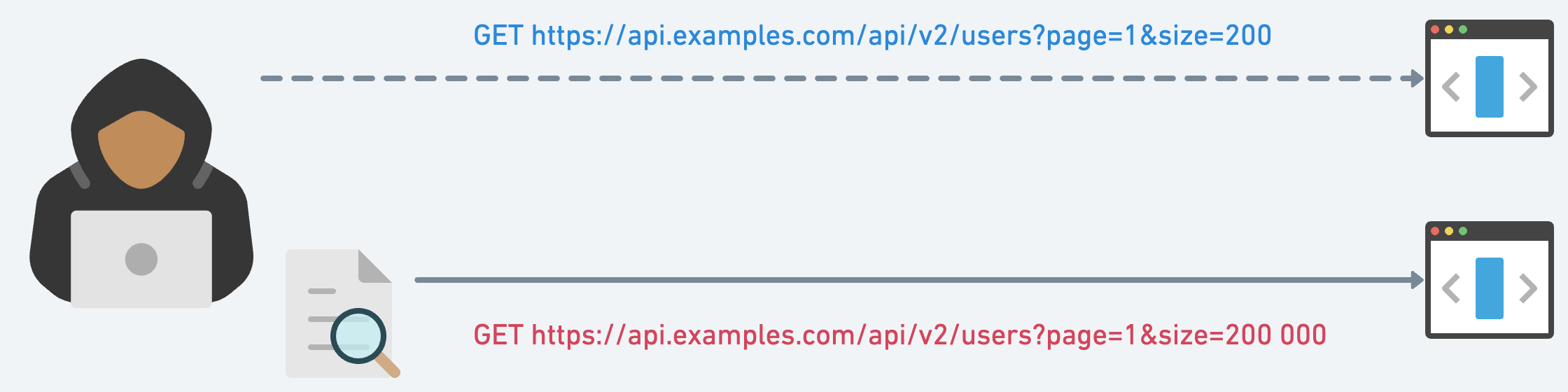
The Flaw: Some APIs, in their generosity, offer unlimited resources. They don’t set boundaries, leading to overconsumption and, eventually, a food (read: data) coma.
The Drama: In the vast landscape of APItopia, some restaurants (APIs) don’t realize that offering unlimited resources can lead to resource exhaustion, skyrocketing bills, and even a complete shutdown.
🛠️ The Recipe for Disaster: Code Exposed
Backend Code (Before Fix):
@app.route('/api/sendSMS', methods=['POST'])
def send_sms():
phone_number = request.json.get('phone_number')
sms_service.send_sms(phone_number, "Your reset code is 1234")
return "SMS sent!"
This code, when triggered, sends an SMS to the provided phone number. There’s no rate limit, meaning it can be exploited to send numerous SMS messages, leading to high costs.
Backend Code (After Fix):
from flask_limiter import Limiter
limiter = Limiter(app, key_func=get_remote_address)
@app.route('/api/sendSMS', methods=['POST'])
@limiter.limit("5 per minute")
def send_sms():
phone_number = request.json.get('phone_number')
sms_service.send_sms(phone_number, "Your reset code is 1234")
return "SMS sent!"
With the fix, the backend now limits the number of SMS messages that can be sent to 5 per minute, preventing potential abuse.
🎭 The Culinary Chronicles: Real-World Exploits
Scenario #1: “ChatterBox”, a popular messaging app, has a “forgot password” feature. Users receive a reset code via SMS. But a mischievous user, Bob, discovers he can trigger thousands of SMS messages, leading to a hefty bill for ChatterBox.
Scenario #2: “PicPerfect”, a photo-sharing platform, allows users to upload profile pictures. Once uploaded, the platform generates various thumbnails. But Alice, a crafty user, exploits the system by uploading multiple images simultaneously, causing a server meltdown.
Scenario #3: “CloudCraze”, a cloud storage provider, allows users to download large files. When a file is updated, all users start downloading the new version. But without any consumption cost alerts, CloudCraze is hit with an astronomical bill at the end of the month.
 |
|---|
| “Why did you feed me so much?" |
🍴 Setting Boundaries: Prevention Tips
- Portion Control: Use solutions like Containers or Serverless code to set limits on memory, CPU, and other resources.
- Size Matters: Define maximum sizes for all incoming data, from string lengths to file uploads.
- Pace Yourself: Implement rate limiting to control how often a client can interact with the API.
- Check the Menu: Add server-side validation for query parameters, especially those controlling data volume.
- Keep an Eye on the Bill: Set spending limits for third-party services. If that’s not possible, configure billing alerts.
📚 The Gourmet Guide: Further Reading
- OWASP’s Culinary School:
- External Cookbooks:
In the grand kitchen of APIs, it’s essential to serve data generously but responsibly. Always remember, while unlimited buffets are tempting, they can lead to unforeseen consequences. Until our next culinary adventure, code responsibly and bon appétit! 🍽️🔒
 |
|---|
| “APIs: Serve responsibly!" |