After our previous deep dives into the vast universe of APIs, today we’re setting our sights on another intriguing realm: API5:2023 Broken Function Level Authorization. Ready to decode the mysteries? Let’s embark on this enlightening journey! 🚀
 |
|---|
| “Is this function for me?" |
🚫 The Forbidden Chambers: Broken Function Level Authorization
Setting: The sprawling metropolis of APItopia, where every API function is like a room in a grand mansion. But not every room is open for everyone, and that’s where the drama unfolds.
The Flaw: Some doors in this mansion are left ajar, allowing uninvited guests to waltz in. These are the functions that should be restricted but aren’t, leading to unauthorized access.
The Drama: In the vast corridors of APItopia, some doors are mistakenly left unlocked. While some guests respect the boundaries, others, with a mischievous glint in their eyes, seize the opportunity to explore these forbidden chambers.
🛠️ The Blueprint: Code Exposed
Backend Code (Before Fix):
@app.route('/api/admin/users/all', methods=['GET'])
def get_all_users():
return jsonify(database.get_all_users())
This code, when accessed, fetches details of all users. There’s no authorization check, making it a potential goldmine for attackers.
Backend Code (After Fix):
@app.route('/api/admin/users/all', methods=['GET'])
@require_admin
def get_all_users():
return jsonify(database.get_all_users())
With the fix, the backend now checks if the user has admin privileges before fetching user details, ensuring that only authorized personnel can access this data.
🎭 The Chronicles of APItopia: Real-World Exploits
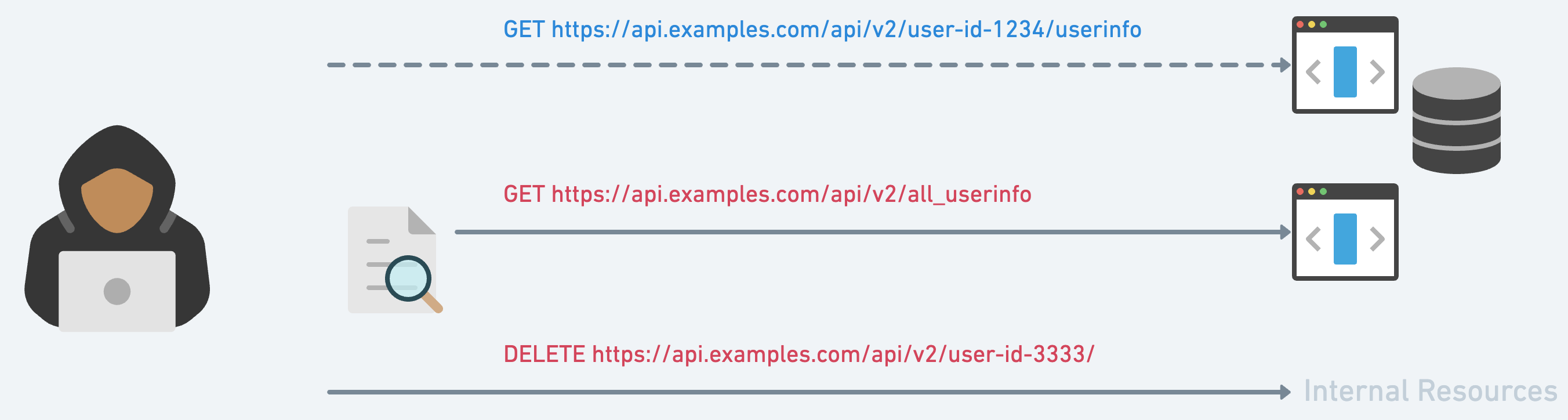
Scenario #1: “InviteMe”, a premium social platform, allows users to join only via invites. During registration, an API call fetches invite details. But Tom, a curious user, discovers he can craft his own invite with admin privileges. By manipulating the API endpoint, Tom grants himself unrestricted access, turning the tables on the platform.
Scenario #2: “DataDome”, a data analytics platform, has a hidden chamber: an API endpoint revealing details of all its users. Alice, a savvy hacker, stumbles upon this endpoint. With a few educated guesses, she accesses this treasure trove of data, jeopardizing the privacy of thousands.
 |
|---|
| “Looking for unlocked doors in APItopia." |
🚪 Securing the Mansion: Prevention Tips
- Guard the Doors: Implement a consistent authorization module that’s invoked across all business functions.
- Default to ‘No Entry’: The enforcement mechanism should deny all access by default, granting access only to specific roles for specific functions.
- Review the Blueprints: Regularly review your API endpoints for function level authorization flaws. Understand the business logic and role hierarchies.
- Strengthen the Locks: Ensure that administrative functions have robust authorization checks based on user roles.
- Trust, but Verify: Even if a function seems non-administrative based on its URL path, always implement authorization checks.
📚 The Grand Library: Further Reading
- OWASP’s Archives:
- External Tomes:
In the grand mansion of APIs, every function is a room with its own secrets. As guardians of this mansion, it’s our duty to ensure that only the right guests enter the right rooms. Until our next adventure, code wisely and stay vigilant! 🏰🔒
 |
|---|
| “Guardian of the API functions” |