As we continue our journey through the vast universe of APIs, today we’re venturing into the mysterious realm of API7:2023 Server Side Request Forgery (SSRF). Ready to decode the secrets? Let’s dive deep into this enigma! 🚀
 |
|---|
| “Exploring the hidden portals of APItopia” |
🌀 The Enigmatic Portals: Server Side Request Forgery
Setting: The vast expanse of APItopia, where every API function is like a portal. Some portals lead to wondrous places, while others can lead to treacherous terrains if not guarded properly.
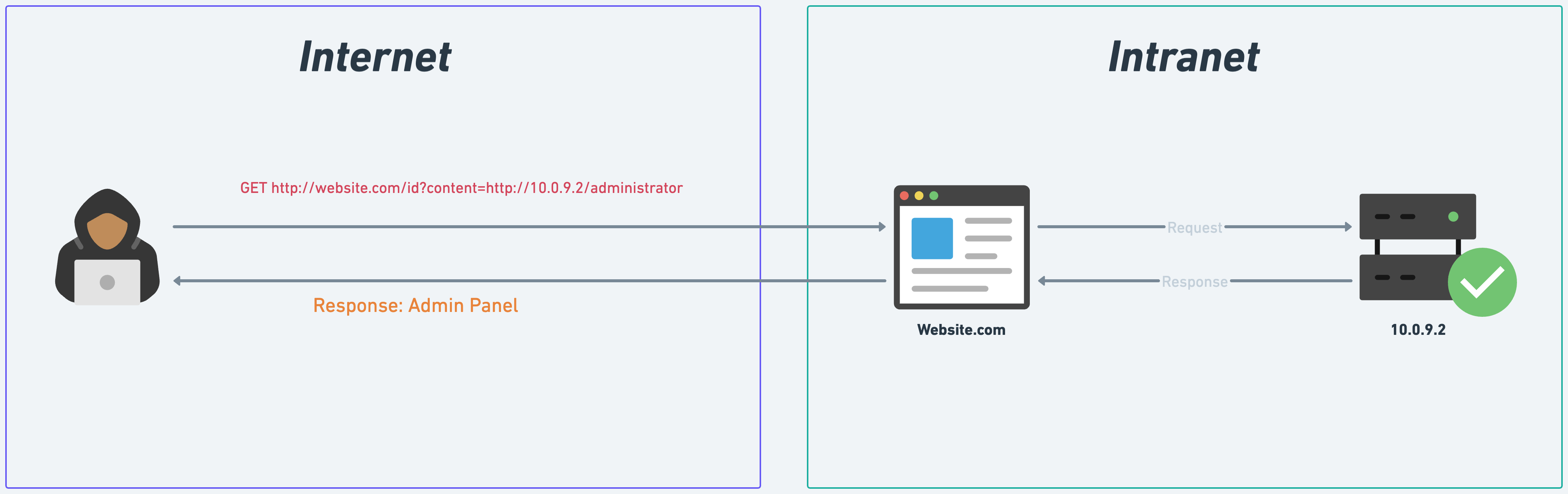
The Flaw: Certain portals, representing server-side requests, can be manipulated to lead to unintended destinations, allowing malicious entities to exploit them.
The Drama: In the intricate world of APItopia, portals are meant to transport data to specific destinations. However, when these portals are manipulated, they can lead to unintended places, causing chaos and disrupting the harmony of APItopia.
🛠️ The Blueprint: Code Exposed
Backend Code (Before Fix):
@app.route('/api/fetch', methods=['POST'])
def fetch_resource():
url = request.json.get('url')
return requests.get(url).content
This code, when accessed, fetches content from any given URL. But what if someone uses it to access internal resources?
Backend Code (After Fix):
ALLOWED_DOMAINS = ["example.com", "trustedsource.com"]
@app.route('/api/fetch', methods=['POST'])
def fetch_resource():
url = request.json.get('url')
if any(domain in url for domain in ALLOWED_DOMAINS):
return requests.get(url).content
return "Access Denied!"
With the fix, the backend now checks if the requested URL belongs to a list of allowed domains, preventing unauthorized access.
🎭 The Chronicles of APItopia: Real-World Exploits
Scenario #1: “PicParadise”, a popular social platform, allows users to fetch profile images from external URLs. Alice, a user, provides a URL, and the platform fetches the image. But Bob, a mischievous hacker, provides an internal URL, initiating a port scan within the platform’s network. By analyzing response times, Bob discerns which ports are open.
Scenario #2: “Securify”, a renowned security product, integrates with various monitoring systems using webhooks. During integration, it sends a test request to the provided webhook URL. Eve, a cunning hacker, provides a URL to an internal cloud metadata service. The platform fetches sensitive cloud credentials, which Eve later exploits.
 |
|---|
| “Decoding the enigmatic portals of APItopia” |
🚪 Guarding the Portals: Prevention Tips
- Know Your Portals: Understand the purpose of each portal (API endpoint) and the potential risks associated with it.
- Guard the Gates: Implement robust authorization and validation mechanisms to prevent unauthorized or unintended access.
- Whitelist Destinations: Maintain a list of allowed domains or URLs and ensure that only requests to these destinations are processed.
- Avoid Raw Responses: Do not send raw server responses to clients. This can expose sensitive information.
- Use Trusted Parsers: Employ well-tested and maintained URL parsers to avoid inconsistencies and vulnerabilities.
- Stay Alert: Monitor your APIs for unusual activity. Set up alerts for potential threats.
📚 The Grand Library: Further Reading
- OWASP’s Archives:
- External Tomes:
In the vast expanse of APItopia, every portal has its significance. As guardians of this realm, it’s our duty to ensure that these portals lead to the right destinations. Until our next adventure, code wisely and stay vigilant! 🏰🔒
 |
|---|
| ““Guardian of the API portals” |